12.7 Testing DKIM
Once you have created your DNS entries and LISTSERV configuration for DKIM, you will want to test it.
12.7.1 LISTSERV’s Deliverability Assessment report
LISTSERV has a built-in Deliverability Assessment report which can be reached in the web interface at Server Administration -> Site Configuration -> Deliverability Assessment. The first screen looks like the following:
Figure 12-1 Deliverability Assessment - Initial Screen
Unless you have multiple domains set up in LISTSERV, there should be no reason to change the pre-populated values. If they are correct, simply click Submit. This will yield the following report:
Figure 12-2 Deliverability Assessment - Report Screen
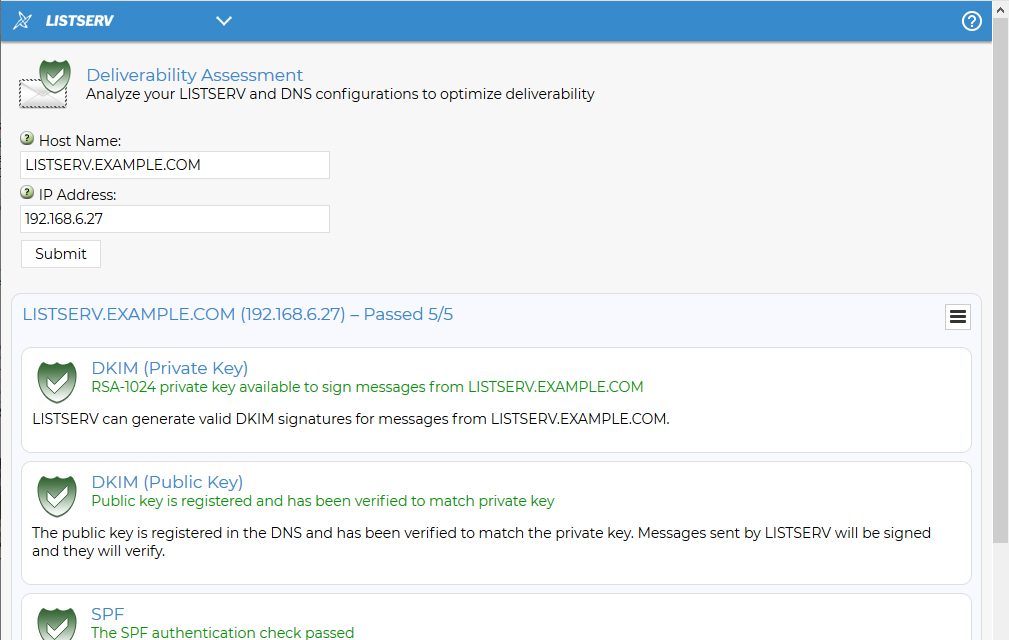
The green shields indicate that, so far as LISTSERV is concerned, you have properly configured the DKIM DNS entry, and LISTSERV itself is properly configured to sign outbound messages with DKIM. If either or both of the shields are not green, you need to recheck your DNS entry and LISTSERV configuration, and correct any errors before running the report again.
12.7.2 Testing the DNS entries
Once you have created the DKIM DNS entries, you can check them with NSLOOKUP or DIG to ensure that they are being served properly by the DNS server:
If you use NSLOOKUP to check the record after you create it, you’ll see something like this:
> set type=txt
> default._domainkey.listserv.example.com
Server: google-public-dns-a.google.com
Address: 8.8.8.8
Non-authoritative answer:
default._domainkey.listserv.example.com text =
“v=DKIM1; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDwl88WzSt
oOTznXCeMJF+J0XDaxrRYgl42hx+zZ4MUAaI8ZCsaozbK4RiCjAt8TUSf4JuEn8mqTK
MfL4Rxf0SEcgEPyJSq1j9AxU3e8ERx5GXj2kJw6lOxIa+Fh0WTcKNImgKz9gMUUL7ls
LnBPghNCCdUvnmYpLhS2HMR1EFrDwIDAQAB”
>
and
> set type=txt
> _domainkey.listserv.example.com
Server: google-public-dns-a.google.com
Address: 8.8.8.8
Non-authoritative answer:
_domainkey.listserv.example.com text =
“o=~”
>
To test the functionality of the DKIM DNS entries, you will probably want to use an online service. One such service is MXToolBox.com. They provide a DKIM Lookup tool that is both free and easy to use, located at https://mxtoolbox.com/dkim.aspx . Simply enter the domain name (for example, “listserv.example.com”) and the selector (for example, “default”) into the two text boxes on that page and click the button for DKIM Lookup. This presents an in-depth report that you can use to verify whether or not your DKIM TXT record has been properly created.
There are many other testers out there; the MXToolBox tester is simply the one that we tend to use at L-Soft. Other testers include https://www.mail-tester.com/spf-dkim-check and https://www.dmarcanalyzer.com/dkim/dkim-check/ ; many more are available via a web search.
12.7.3 Testing DKIM signatures on email
Finally, the simplest way to test that LISTSERV is actually signing emails properly is to create a test list, add an external test account to it (e.g., a GMail account) and send mail to the list.
In the mail headers for the message received by the test account, you’ll see something like the following:
DKIM-Signature: v=1; a=rsa-sha256; d=LISTSERV.EXAMPLE.COM; s=DEFAULT; c=relaxed/relaxed; bh=wCPfXJT/+EjG2NI/0kOFZQI3luKHV0YjC+ZO6gi9sW8=; i=@LISTSERV.TD.COM;
h=Date:Sender:From:Subject:To;
b=b9p4Vj9NSsMxTIRwhO1oRYTYovn8UT/
This is the DKIM signature added by LISTSERV as the message was processed and distributed.
|
|
Note: The signature will not appear to match either of your DKIM keys; this is because the signature is generated on a per-message basis using the private key in the appropriate *.DKIM file you created and installed earlier. |
Above the DKIM-Signature header will be a header showing that the message was properly authenticated:
Authentication-Results: mx.google.com;
dkim=pass header.i=@LISTSERV.EXAMPLE.COM header.s=DEFAULT header.b=b9p4Vj9N;
spf=pass (google.com: domain of owner-nolist-test-20160331-set*john*-doe**gmail*-com@listserv.example.com designates 192.168.6.27 as permitted sender) smtp.mailfrom=owner-nolist-TEST-20160331-SET*john*-doe**GMAIL*-COM@listserv.example.com;
dmarc=pass (p=NONE sp=NONE dis=NONE) header.from=example.com
Since we used a GMail account, the above is how Google reports the results. In this case, the message not only passed DKIM testing, but also SPF and DMARC (meaning that this particular LISTSERV server is very well provisioned for mail reputation). Other ISPs will produce similar test results, although the formatting may vary depending on the mail product used on the receiving end.
It should be noted that Yahoo, which originally promulgated the now-deprecated DomainKeys standard, will also produce results for their standard, even though LISTSERV uses DKIM:
Authentication-Results: mta4010.rog.mail.bf1.yahoo.com
from=listserv.example.com; domainkeys=neutral (no sig);
from= LISTSERV.EXAMPLE.COM; dkim=pass (ok)
However, Yahoo is also authenticating against the new DKIM standard, so as long as DKIM gets a “pass”, it doesn’t matter that you did not provide a DomainKeys signature.
